Category: Linux
-
Getting all your repos with corresponding architecthre
Getting all your repos with corresponding architecthre requires surprise amount of API shinnanigans! Dockerfiles/list.sh at main · shaman007/Dockerfiles
-
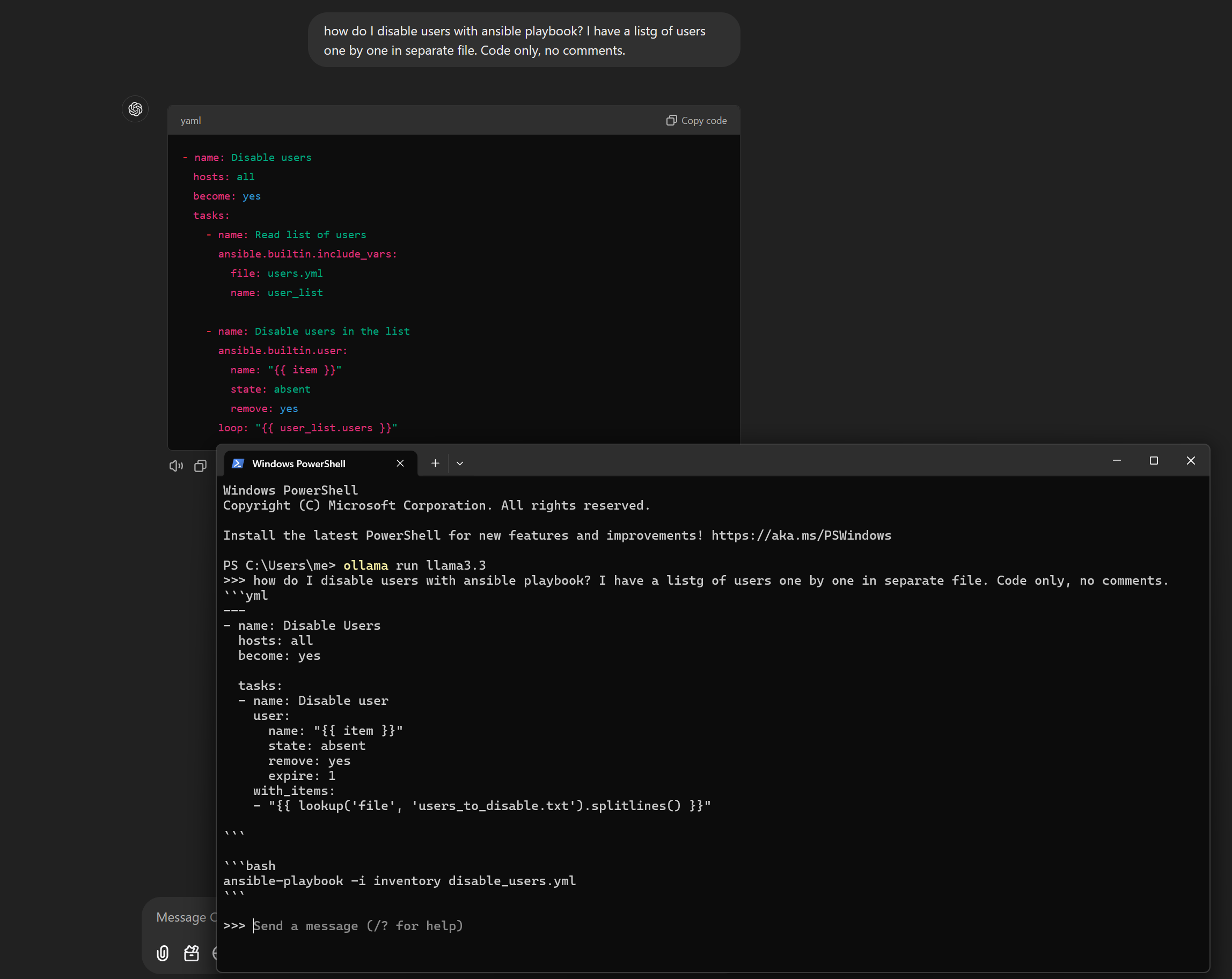
Gpt 4o vs llama 3.3
-
Sieve shinannigans
Welp, if you’re using Sieve with the Dovecot (like you should), the client may behave strange, due to Sieve needs some dot-files and they naturally may come in your mailbox/maildir dir. Some clients are aware, some clients not, but the best way is to put dotfiles somewhere else. Like: Otherwise errors/warnings in the logs, like…
-
Yet another cluster update
UniFi: made a deployment and network setup. Does not see AP’s. 10001 UDP seems to be a problem, yet no idea why. Adopted them manually via SSH, now they work. Yes, consumes RAM for no reason. Why? No idea. However, the functionality is limited compared to the Windows app, and it does not provide me…
-
Cluster update
Out of all services, only Mastodon and UniFi Network controller are left, both are technically possible, but require strange things. Own Bitwarden service works great, however, needs a license to be OTP key. The Minecraft server works great. Done log aggregation, local Docker registry, metrics to have them in Lens, backups of everything. The phone…
-
OrangePi 5b emmc support
Armbian image from https://www.armbian.com/orangepi-5/ by default thinks that the board is 5, not 5b, so no nice emmc storage for you! I thought that it’s kind of general issue with the kernel, but all it took is to change fdtfile to rockchip/rk3588s-orangepi-5b.dtb in the /boot/armbianEnv.txt. Now my /var with all K3S and rancher stuff is…
-
Nexcloud is getting better
It can do really neat things, as it turned out!
-
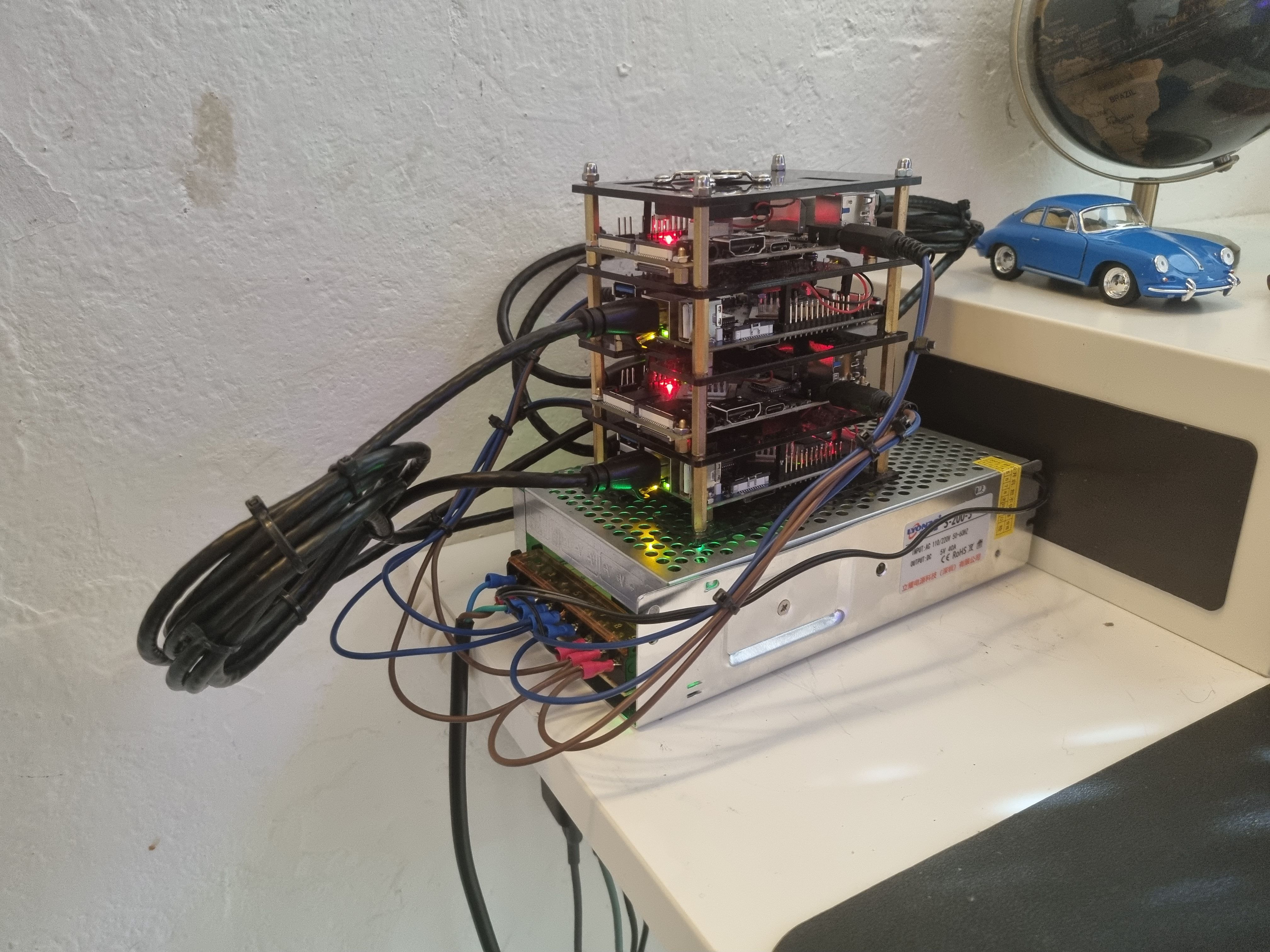
Cable-managed the K3S this blog hosted on
Looks nicer! I’d used 200 Wt power supply so it wouldn’t struggle and maybe I would add some more hardware from the closet with router and stuff to it.
-
Turris MOX (openwrt) Prometheus exporter
It works! The exported could be downloaded from here: GitHub – prometheus/collectd_exporter: A server that accepts collectd stats via HTTP POST and exports them via HTTP for Prometheus consumption. To build it just install golang and gcc, in case of the “/usr/bin/ld: cannot find -lpthread” error just create an empty AR archive somewhere in the…