-
My blog
I write mostly about security, mail, web and linux. My contacts are: mail://me@andreybondarenko.com and shaman007 all around Telegram, FB chat, WhatsApp. Primary use me@andreybondarenko.com and @shaman007:matrix.andreybondarenko.com Buy me a beer / Автору на пиво: shaman007@andreybondarenko.com (paypal)17QxrNyk9BCrP6LGUbqCNnXCzu4oeoYKaH (btc) 0x57500960FBC986225209E597D5B97065A9A10043 (eth) Links turned out to be useful / не потерявшие актуальности ссылки: Растаможка автомобиля из России в ЧехииПоиск работы…
-
Getting all your repos with corresponding architecthre
Getting all your repos with corresponding architecthre requires surprise amount of API shinnanigans! Dockerfiles/list.sh at main · shaman007/Dockerfiles
-
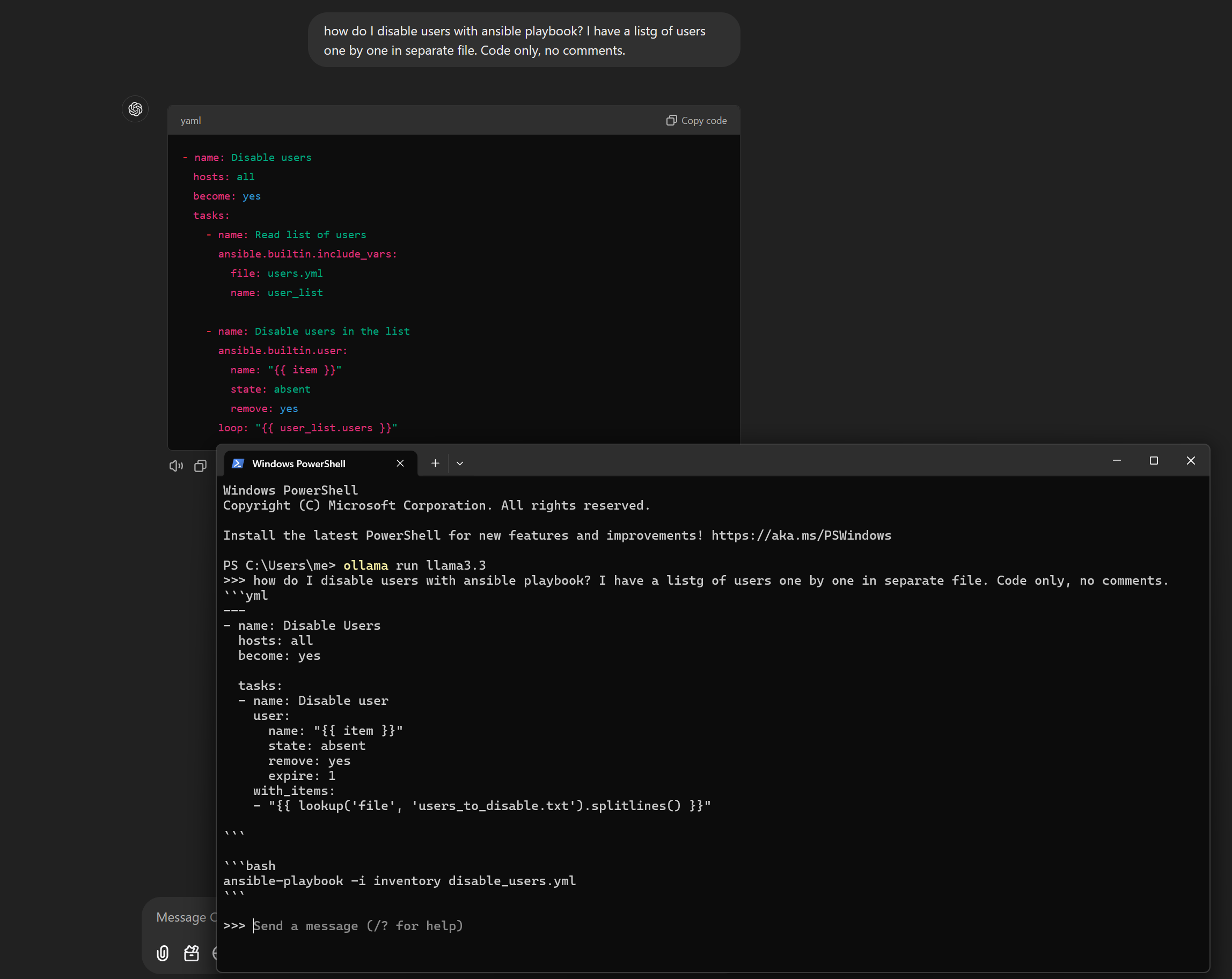
Gpt 4o vs llama 3.3
-

My family as Chat GPT 4o sees it
-
Sieve shinannigans
Welp, if you’re using Sieve with the Dovecot (like you should), the client may behave strange, due to Sieve needs some dot-files and they naturally may come in your mailbox/maildir dir. Some clients are aware, some clients not, but the best way is to put dotfiles somewhere else. Like: Otherwise errors/warnings in the logs, like…
-

Recent photo of this site
-
На злобу дня
У меня есть мнение насчет последних событий с неким Павлом, которое я оставлю при себе. Но вот эта уверенность людей в том, что “компании могут/будут/хотят заботиться о моей приватности”, особенно в контексте некоего Павла… Смотрите, быстрый privacy-101: – информация, которую вы не хотите раскрывать никому не должна попадать в места, в контроле которых вы не…
-
Резервное копирование: как не плакать
Навеяно постом адвоката Сологуба, который я воспринял близко к сердцу: потеря архива документов для меня – страшный сон. А тут – чужие документы! DISCLAIMER: Я не буду долго расписывать теорию и почти не коснусь события “ОБЫСК“. Я буду считать, что хранимое не приводит к гибели людей или серьезным потерям юрлиц. Будем считать, что у вас…
-
Hardware upgrade
Now there are 4 OrangePI 5 there with NVME SSD storage and Ubiquity switch.
-
Yet another cluster update
UniFi: made a deployment and network setup. Does not see AP’s. 10001 UDP seems to be a problem, yet no idea why. Adopted them manually via SSH, now they work. Yes, consumes RAM for no reason. Why? No idea. However, the functionality is limited compared to the Windows app, and it does not provide me…
-
Cluster update
Out of all services, only Mastodon and UniFi Network controller are left, both are technically possible, but require strange things. Own Bitwarden service works great, however, needs a license to be OTP key. The Minecraft server works great. Done log aggregation, local Docker registry, metrics to have them in Lens, backups of everything. The phone…
Got any book recommendations?